Lessons I Learned From Tips About How To Build A Security Policy
![Cybersecurity Best Practices For 2022 [15 Data Protection Methods] | Ekran System](https://image.slidesharecdn.com/importanceofasecuritypolicy-13281642117262-phpapp01-120202003227-phpapp01/85/importance-of-a-security-policy-13-320.jpg?cb=1659364538)
It enables to identify and record security risks.
How to build a security policy. There are two common approaches to application migration: All punishments are not created. A security policy should also clearly spell out how compliance is monitored and enforced.
Make security policies and documentation welcoming. Make sure end users have read and understood the policies. To mitigate this risk, you can configure the network access:
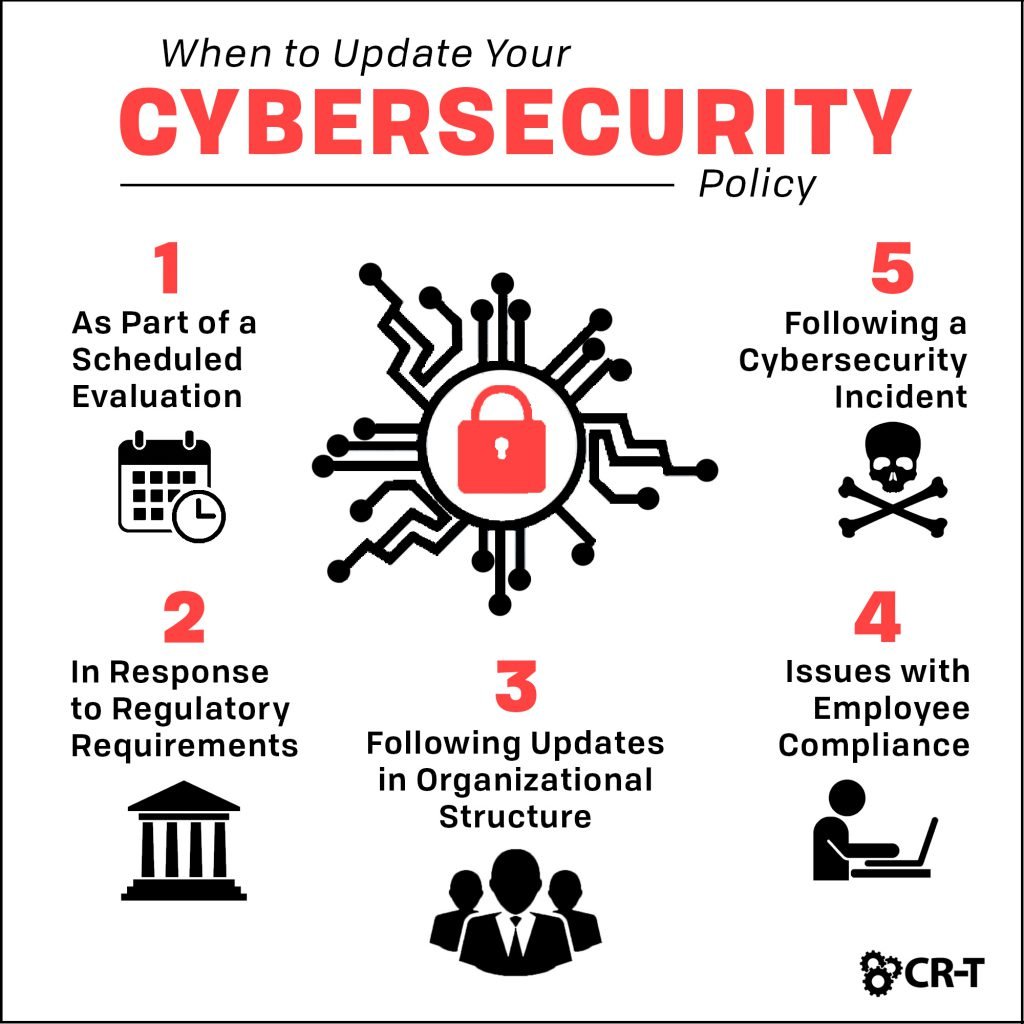
Establish effective communications within the organisation to ensure that every team is following good cybersecurity hygiene. Performing the following steps to develop a security policy talk with other members of your organization, such as security auditors, to better determine your security needs. To configure a setting using the local security policy console to open local security policy, on the start screen, type secpol.msc, and then press enter.
Helps meet regulatory and compliance requirements. Define that applicable parties should provide. Identify your risks what are your risks from inappropriate use?
Policy definitions added to the initiative that have parameters are displayed in a grid. Security lighting is a very important aspect of a robust. Whether it’s using tools like notion or google docs, or even adding commenting to your internal knowledge base, ensure.
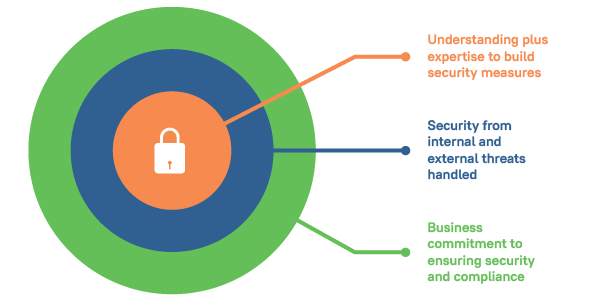
Policies should be designed around your team’s organization structure, technologies, and security and compliance needs. Begin with perimeter security, making sure that you’re using fences, gates, guards and video surveillance around the perimeter. Restrict clients allowed to make remote calls to sam security policy setting to force the security accounts.




![Cybersecurity Best Practices For 2022 [15 Data Protection Methods] | Ekran System](https://www.ekransystem.com/sites/default/files/15%20best%20cybersecurity%20practices/figure-15.jpg)





![How To Build A Cyber Security Policy [5 Tips]](https://www.soscanhelp.com/hs-fs/hubfs/Policy%20Edited.png?width=650&name=Policy%20Edited.png)


![How To Build A Cyber Security Policy [5 Tips]](https://www.soscanhelp.com/hubfs/Business%20Meeting%20Header.png)

